Orcmid's Lair |
||||
|
|
2004-06-02Whose Computer Is It: All Your BIOS Are MineSlashdot | Intel To Release Next-Gen BIOS Code Under CPL. The initiative is part of the Extensible Firmware Interface and it allows for the pre-boot software that operating systems can depend on to establish themselves above the hardware and, indeed, to be "booted" at all. While this goes on deep in the plumbing of PCs, it has an important and crucial role in providing platform-adaptable software that works across vendors (Dell, H-P, IBM, and the guys on the corner who build PCs in the back of their store). Here's more. Buried inside every PC descended from the IBM PC architecture there is ROM-stored software code that starts things off. Running at POST (Power-On-Self-Test) Time, the startup software (1) is the first program that runs when the CPU chip wakes up, (2) detects and connects the locally-installed devices and awakens whatever other firmware there is that needs to be operating in coordination with the processor, and (3) initializes a layer of software and data that can be used to access the computer's configuration through standard programmatic interfaces. This procedure provides a rudimentary configuration and ready-to-hand software environment that is the basis for finding and bootstrapping the code for any operating system that will then be allowed to run, pretty display gui-gaws and all. Every PC operating system relies on this pre-existing ready-set-go stage as a way for being awakened and then drawing itself up to full, wakeful height, like a slumbering genie aroused through a startup incantation. Linux distributions, FreeBSD, MS-DOS, Windows flavors, Solaris on Intel, and any other operating systems that might have a claim on your attention to a PC are all designed to arise under control of the same startup software, relying on its provisions to determine what's up and how to establish their own presence and operation as your eager servant. In the usual manner of conceptual corruption, this permanently-installed setup and hardware coordination software is called the BIOS (Basic Input-Output System). The term has murky origins in DOS (Disk Operating System) for the original IBM System/360 1964 models and in other software exhibiting some fledgling qualities of operating-systemness before that. The particular arrival on your desktop traces its lineage back through CP/M realizations at the turn of the 1980s or the Apple II firmware of the same era. 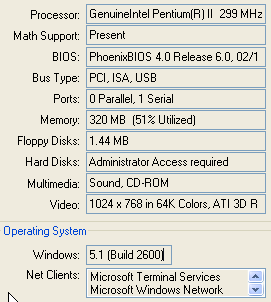 You might not observe the influence of this software ever, unless you have some occasion to interact with what is called your computer's setup procedure, a program that is always there and gives you some influence over the basic processes of the computer and the startup rules that, with all-fingers-crossed care, can be varied to reflect special requirements you might have. If (as is often controlled by such a startup parameter) your computer displays messages from the startup processes carried out before the OEM-installed operating-system software splashes onto your screen, you will see evidence of the configuration-determination process as devices and the BIOS itself are identified. And you will have that wonderful affirmation that all of that bargain-basement RAM you upgraded with is present and every bit is accounted for. You might not observe the influence of this software ever, unless you have some occasion to interact with what is called your computer's setup procedure, a program that is always there and gives you some influence over the basic processes of the computer and the startup rules that, with all-fingers-crossed care, can be varied to reflect special requirements you might have. If (as is often controlled by such a startup parameter) your computer displays messages from the startup processes carried out before the OEM-installed operating-system software splashes onto your screen, you will see evidence of the configuration-determination process as devices and the BIOS itself are identified. And you will have that wonderful affirmation that all of that bargain-basement RAM you upgraded with is present and every bit is accounted for.Depending on the operating system, there are programs such as Norton Utilities that present the configuration details from the BIOS and those further accretions provided as part of operating-system richness. You'll also see that the BIOS is someone's intellectual property. Not yours. Although it is the combination of processor, BIOS, and mother-board adapters that are the substrate on which your PC's capabilities are anchored, it is the BIOS and its protocols and interfaces that provide the fulcrum by which the operating system levers its way into operation. It is the balance point on which the great wheel of hardware attracting operating-systems attracting application developers attracting users attracting commodity hardware spins. The BIOS as critical point is not lost on those who see the opportunity of the commodity PC economy. Others, recognizing the BIOS as a vulnerability to substitutions and competition, have worked to protect theirs. At one point, Apple Computer endeavored to close out unlicensed software developers from making direct use of interfaces to the Apple II BIOS (essentially the whole operating system at that time). Those who want to clone Apple computers have learned that the property rights to the BIOS code are jealously protected. The same goes for embedded computer systems, where automobile manufacturers are extremely reluctant to describe access to their computer interfaces by non-factory-authorized and -licensed service organizations. Whether you ever notice where the BIOS is stored in your computer, and ever have any need to know its functions, the fact of its honoring an open or a closed specification will be reflected in the robustness of the developer community and the diversity of suppliers and users.
May your heart always be joyful
Comments:
Post a Comment
|
|||

